Secure SDLC
This blog post emphasizes the importance of integrating security throughout the SDLC, known as Secure SDLC, to reduce costs, improve collaboration, ensure compliance, and enhance product value while advocating best practices like the shift-left approach, a security-first culture, and continuous scanning.
What is the SDLC?
In the 1970s, ad-hoc development, creating projects ‘on the fly’ per se or without structure, was the most commonly used method for software development. However, ad-hoc was disorganized, time-consuming, and did not prioritize the quality of applications being produced. Professionals in the field recognized the need for structure in development frameworks, leading to the introduction of the software development life cycle (SDLC)—a well-defined set of phases intended to guide the process of creating software applications. Unlike ad-hoc, the SDLC maximizes efficiency, reduces costs, and delivers applications in record time. Additionally, it is an iterative process, allowing for continuous improvement and higher quality of applications.
Phases of the SDLC include:
- Planning involves analyzing consumer needs, defining requirements (cost, resources), and project scope, as well as outlining compliance standards.
- During the design phase, teams create a design that aligns with project requirements, minimizes cost, and efficiently uses resources. This plan is then reviewed by stakeholders, who will offer feedback, allowing team members to make improvements and iterate upon the design.
- Implementation encompasses defining standard coding guidelines for teams, software creation, and integration with existing features.
- Testing/verification involves using a diverse suite of testing methods to identify weaknesses/failing areas of code and remediate them, ensuring the application works effectively.
- During deployment/maintenance, the application is deployed to the consumer base and vigilantly monitored by security/developer teams for bugs, security concerns, etc.
As the SDLC is often confused with the software supply chain (SCS), it’s important to recognize the key distinction between the two: SDLC refers to the framework that helps organizations maneuver their way through software development whereas SCS refers to all components—including people i.e engineers, developers—involved in the software development process.
Benefits of SDLC Security
In the age of agile development, addressing security concerns at the earliest stages of the SDLC is a critically important strategy due to mounting security and compliance concerns that arise with rapid updates to source code. The benefits of prioritizing security at the earliest stages of the SDLC include:
- Reduced time and costs: Improved security allows for early detection of issues and consequent reduction in mean time to remediate (MTTR) and development costs
- According to the National Institute of Standards and Technology (NIST), lack of proper security measures can increase development costs up to 100-fold[1].
- Seamless collaboration: Integrating security with the SDLC creates greater transparency and visibility between developer and security teams, enabling improved collaboration and a more efficient workflow.
- Elevated product value: Secure SDLC attracts investors and impresses stakeholders while building trust amongst the consumer base.
- Compliance enforcement: Prioritizing security helps ensure organizations are meeting industry-wide compliance and licensing standards, reducing legal risk.
- Improved security/risk reduction: Maintaining security measures ensures organizational and application safety and strength while reducing attack vectors/surfaces and vulnerabilities.
Securing the SDLC
A Secure SDLC carefully integrates thorough security measures into each phase of the SDLC:
- Planning includes outlining security requirements and compliance standards that correspond to project scope and requirements. Security teams should review the product idea and identify security concerns/respond with steps to remediate the finalized plan.
- During the design stage, security teams need to conduct architectural reviews to analyze the security of the various tools, software, and services being used and provide feedback to the design team/developers. It is also important to update security requirements to ensure they align with the evolving design model.
- During the implementation stage, the priority is to ensure the source code is secure. Amongst developer teams, industry-standard code security guidelines (such as NIST 800-218 SSDF) are utilized. Security teams conduct comprehensive code reviews using a diverse set of application security tools (ASTs). Common ones include software composition analysis (SCA), which helps manage vulnerabilities within the application’s open source inventory, enforces license and security compliance issues, and offers detailed remediation strategies, and static application security testing (SAST), a white box testing method that performs static analysis on source code to identify security weaknesses.
- Testing/verification includes running a comprehensive suite of tests and scans to examine code for security vulnerabilities. Some popular testing methods at this stage include penetration tests, essentially simulating cyberattacks upon code to expose blind spots, and dynamic application security testing (DAST), a black box testing method that pinpoints vulnerabilities in the running application.
- During deployment/maintenance, the application is monitored by security teams for unusual activity: potential breaches, bugs, new vulnerabilities that arise in the open source inventory, and more. Security teams should outline an incident response document, with descriptions of potential incidents and detailed steps for remediation, to streamline maintenance.
What is ASPM?
Though the Secure SDLC offers a strong security framework, it can also feel disjointed because of the many applications, tools, and methods that must be implemented (the average app security team uses around 60-70 different tools)[2], each of which offers distinct information that must be manually parsed, understood, and then compiled into a set of actionable insights. Application security management (ASPM) is a comprehensive approach to app security that significantly reduces manual labor and mean time to remediate (MTTR) by utilizing a diverse suite of ASTs to identify the most critical vulnerabilities—allowing organizations to address the most dangerous risks first—and provide a clear picture of security risk across the SDLC.
ASPM functionalities
Apart from the remediation capabilities mentioned above, ASPM’s key use cases are:
- Vulnerability scanning: ASPM utilizes a diverse toolkit of native and third-party scanners that enable the detection of security weaknesses, including SCA and SAST.
- Risk management: ASPM delivers consolidated information garnered from its diverse suite of ASTs, rather than individual insights collected from separate tools that need to be manually contextualized and prioritized. As a result, ASPM usage has been reported to reduce ‘noise’ (security alerts, notifications, etc.) by 90%, allowing organizations to hone in on the most critical issues.
- Reporting: ASPM generates a wide variety of reports—such as vulnerability overview reports and code digests on changes made in source code management platforms—to help organizations and security personnel gain insight into application security and motivate their next steps. ASPM also automatically enforces industry-wide compliance and security standards, generating compliance reports to identify areas of the application that are not up to par.
Core components of ASPM
ASPM aims to secure the various attack vectors/surfaces across the SDLC by focusing on three core components:
- Application security: ASPM involves implementing various protective measures to secure the application as it moves through the SDLC. For this purpose, ASPM utilizes various native and third-party tools/scanners:
- SCA: Detects vulnerabilities in open-source inventory, dependencies, and third-party libraries. According to “The State Of Application Security, 2024” report by Forrester, only 16% of all security decision-makers planned to adopt software composition analysis in the next 12 months[3].
- SAST: Identifies security flaws in code.
- Infrastructure as Code (IaC) security alerts when misconfigurations are discovered, offers remediation strategies and helps enforce security guidelines for the cloud technologies being used.
- Container scanning examines containers—code, dependencies, open source inventory, etc.—for potential vulnerabilities.
- Pipeline security: ASPM primarily focuses on securing the CI (continuous integration)/CD (continuous delivery) pipeline, which involves automated testing when code is committed and automated deployment of tested code. Automation within CI/CD pipelines allows for the smooth integration of changes to the application and ensures the improved product reaches consumers sooner. Key components of maintaining pipeline security include
- Secret scanning: Scans code for secrets—confidential information i.e. API keys that could put the application at risk—and alerts developers to risks that could compromise application security.
- CI/CD Pipeline Security: Enforces least privilege rules by granting individuals/tools the least amount of access necessary to carry out a task, thereby helping reduce the risk of unauthorized actions.
- Code Leakage Monitoring: Alerts security teams when code is leaked or suspicious activity is detected, helping prevent bad actors/the public from having potentially dangerous levels of access to an application’s internal systems.
- Code Tampering Prevention: Helping maintain application integrity by informing teams when unauthorized changes are made or suspicious activity is observed, preventing alteration of source code/injection of malicious code
- Insecure Coding Practices Detection: Detects risky coding practices—such as hardcoding secrets, misconfigurations with Infrastructure as Code (IaC), and failing to adhere to least privilege and zero trust policies— which can expose crucial, sensitive information to threats.
- Security posture management is an organization’s ability to respond efficiently and effectively to cybersecurity threats. This involves regular assessment and improvement of security measures in response to the evolving cybersecurity landscape.
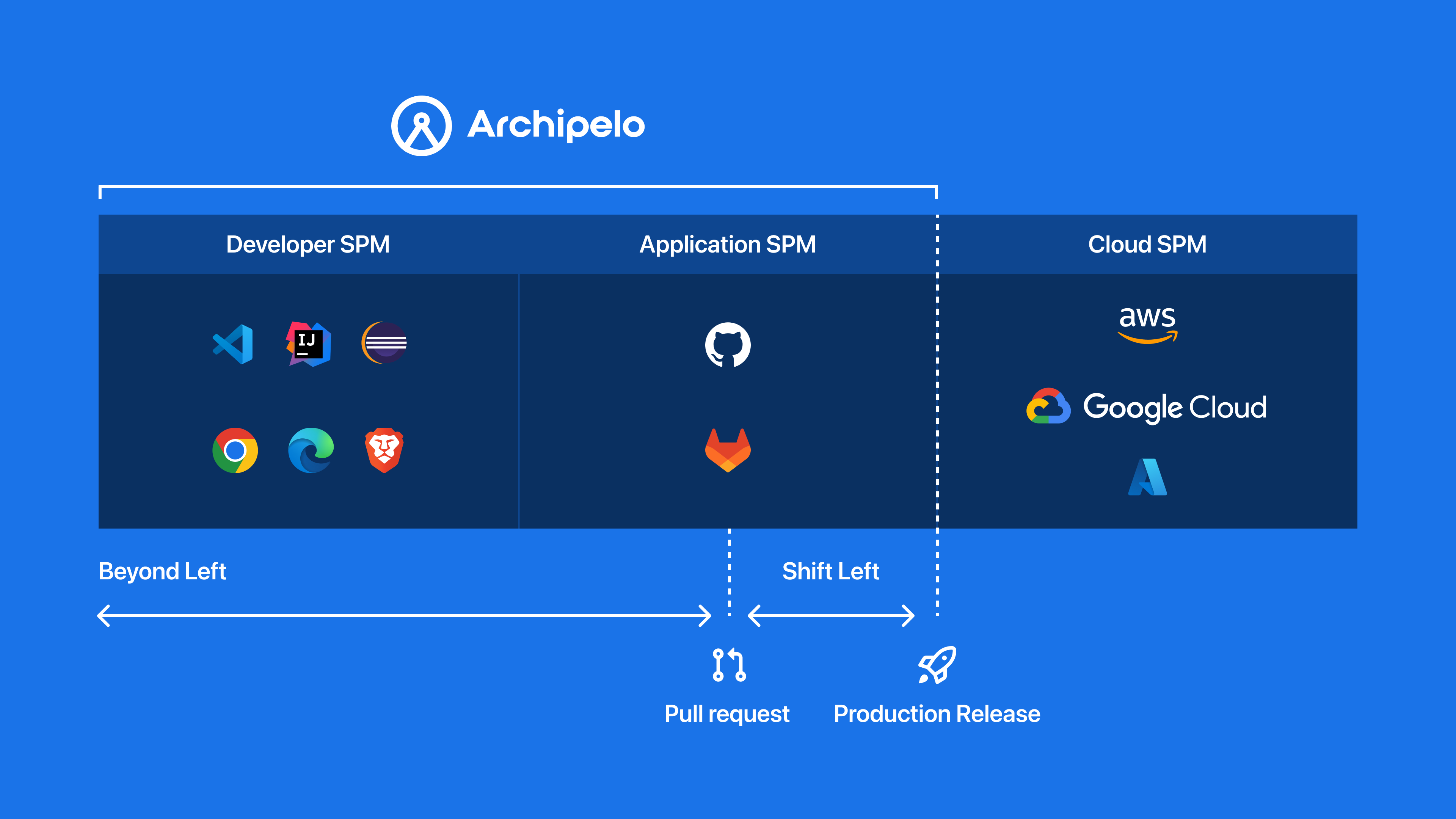
Cloud SPM, ASPM, and DevSPM
While ASPM focuses on securing everything ‘from code to cloud’, Cloud SPM is specifically targeted at securing cloud environments, ensuring the smooth deployment of software applications. Cloud SPM vigilantly monitors the cloud environment, sending alerts when vulnerabilities/concerns (such as misconfigurations and compliance issues) are detected, enabling efficient incident response and secure infrastructure.
While Cloud SPM keys in on the tail-end of the software development process, Developer SPM (DevSPM) aims to transform the cybersecurity landscape by focusing on the individuals that shape it from the beginning—developers. Unlike ASPM, which begins tracking security-related data after code is committed, DevSPM opts for a more holistic view, collecting contextual information and metadata about development activity, such as sites accessed and tools used, even before commits are made. With the rapid rise of AI-generated code, DevSPM becomes especially important as it helps verify the origin of/tracks changes to code, detects threats early—reducing MTTR, and creates a knowledge base of insights gleaned from the development process.
Best practices to integrate security into SDLC
- Shift-left approach: Before the transition to agile software development, developers prioritized efficiency, velocity, and speed, often treating security as an afterthought. With the rise of agile development and an evolving cybersecurity landscape, ‘shifting left’ or integrating security with earlier/the leftmost stages of the SDLC has proven extremely beneficial for organizational growth and well-being, allowing for early detection and remediation of issues.
- Security-first culture: Until recently, security and development were treated as two separate spheres. Facilitating collaboration and knowledge exchange between teams is essential to cultivating a work culture that prioritizes security. Security awareness training, primarily targeted at developers, builds a foundation for collaboration and educates development teams on the ins and outs of cybersecurity, allowing developers to approach coding/development with a security-first mindset.
- Data documentation: It’s important to keep a running document of security requirements, implemented security measures, and security incidents/suspicious activity. When security issues are detected, teams can refer back to this document to pinpoint what areas need to be improved upon and utilize information about past incident responses to guide their next steps.
- Secure coding guidelines/standards: Developers are a key part of the SDLC and therefore play an immense role in shaping the security of an application. Development teams should work to incorporate key security practices into their work (thereby taking a preventative approach) by following industry-standard secure coding guidelines, such as NIST 800-218 SSDF and OWASP (Open Web Application Security Project) Top 10.
- Continuous scanning: Application security is an essential constant throughout the software development lifecycle. Utilizing scanners, such as SAST and DAST, to continuously monitor the application enables teams to proactively respond to detected threats.
How Archipelo helps with SDLC security
Archipelo is a DevSPM platform that empowers organizations and developers with crucial code provenance and development insights, helping maintain a secure SDLC in a quickly changing technological landscape. Archipelo employs a dynamic security toolkit—including SAST, SCA, Container Security, IaC, software bill of materials (SBOM), and secret scanning. Additionally, Archipelo offers compliance enforcement, code governance (differentiating between human and AI-generated code), and risk monitoring (insights into code changes across the SDLC) services. Unlike its competitors, Archipelo is uniquely positioned ‘beyond left’ in the cybersecurity landscape, enabling early detection and remediation of issues.
Resources
- “The Economic Impacts of Inadequate Infrastructure for Software Testing”, Gregory Tassey, 2002
https://www.nist.gov/system/files/documents/director/planning/report02-3.pdf - “Simplify Cybersecurity With a Platform Consolidation Framework”, Dionisio Zumerle, John Watts, 2024
https://www.gartner.com/en/documents/5314263 - “The State Of Application Security, 2024”, Janet Worthington, Sandy Carielli, 2024
https://www.forrester.com/report/the-state-of-application-security-2024/RES180999
We are Archipelo
At Archipelo, we are committed to empowering organizations to build secure software. Our vision is to achieve this by delivering an intelligent solution that enables security and engineering teams to ensure the highest level of software security and compliance without compromising speed of delivery.
Co Author: Alex Saifulin
Get Started Today
Archipelo helps organizations ensure developer security, resulting in increased software security and trust for your business.
Try Archipelo Now